SaaS security related data breaches through cybercrimes are not a new thing in the digital world. Many businesses and companies have reported unauthorized data access and misuse of confidential information to bring the company down. At an individual level, many have been victims of hackers who use different approaches to gain access to personal computers and take control.
The same problems affect companies that rely on Software-as-a-Service (SaaS) applications. SaaS providers are constantly releasing security patches to make their applications more secure. However, cybercriminals also don’t sleep. They come up with new ways to access sensitive data and sabotage the operation of different companies.
Ensuring data security in the cloud is the responsibility of all parties involved. Both cloud service providers and their clients should use the best SaaS security best practices to protect data. Read on for detailed information about this topic, including the SaaS security checklist.
Who Is Responsible for Security In SaaS?
SaaS vendors are primarily responsible for the data security of any information on their platform. They provide physical, infrastructure, and SaaS applications security against any threats.
However, a SaaS provider does not own the customer data or hold any responsibility for how it is accessed and used. Therefore, security in SaaS remains a collective responsibility of all parties involved. In this case, SaaS providers and customers use their applications.
Cloud consumers are tasked with providing security for the endpoints they use to access SaaS applications. That means you should always adopt the best SaaS security practices and security measures to avoid and combat any threat. You also play a crucial role in protecting sensitive data for your company.
Why Do Enterprise Customers Care About SaaS Security?

About 70% of cloud application users say software quality affects their purchasing decision. That tells cloud providers how much they should invest in developing high-quality SaaS applications.
But 63% of their clients also claim that software data security is their primary concern when purchasing cloud services.
In other words, SaaS providers should take time to patch security loopholes in their applications and implement security measures to appeal to prospective clients. But why do enterprise customers are so obsessed with SaaS security?

It goes without saying that every enterprise customer should protect their IP and their users' data because data breaches are costly, and no company wants to lose its revenues in addressing the aftermath of a cybercrime. That's why enterprises are using SAP penetration testing services to ensure that cloud-migrated ERP systems are secure in addtion to their SaaS solutions.
Because, data breaches cause productivity losses, penalties for non-compliance from regulating agencies, and potential loss of sales and prospects. No enterprise will consider a SaaS service that does not address security threats appropriately. They don’t want to incur losses and ruin their reputation.
Are B2B SaaS Security Controls Different from B2C SaaS Security Controls?
There should be no difference in the security standards of B2B and B2C SaaS solutions. Whether you sell to individuals or businesses, the methods, tools and processes you use to protect your users' data is exactly the same.

Want my team to show you how to put a scaleable SaaS security structure in place?
Businesses and customers using SaaS solutions consider the same factors regarding SaaS security controls. The primary concern in the two cases is addressing the security risks. Any SaaS provider ensures the right set of security controls are applied and defined in both cases. And that is done by monitoring the application’s data and identity protection.
What Are the Key SaaS Application Security Risks & Vulnerabilities?
Web applications are never short of security risks and vulnerabilities. Open Web Application Security Project (OWASP) outlines the most prevalent security threats that SaaS applications and other cloud providers should address. CWE/ SANS also lists the top 25 SaaS application flaws that can let attackers access and control the software, stealing sensitive data. A SaaS provider should address them before releasing the software to the general public.
OWASP top 10 list of vulnerabilities and web application security risks:
Broken Access Control
Cryptographic Failures
Injection
Insecure Design
Security Misconfiguration
-
Vulnerable and Outdated Components
-
Identification and Authentication Failures
-
Software and Data Integrity Failures
-
Security Logging and Monitoring Failures
Server-Side Request Forgery
CWE/ SANS top 25 SaaS application security risks and vulnerabilities:
Out-of-bounds Write
-
Improper Neutralization of Input During Web Page Generation (Cross-site Scripting)
Out-of-bounds Read
Improper Input Validation
-
Improper Neutralization of Special Elements used in an OS Command (OS Command Injection)
-
Improper Neutralization of Special Elements used in an SQL Command (SQL Injection)
Use After Free
-
Improper Limitation of a Path name to a Restricted Directory (Path Traversal)
Cross-Site Request Forgery (CSRF)
-
Unrestricted Upload of File with Dangerous Type
-
Missing Authentication for Critical Function
Integer Overflow or Wraparound
Deserialization of Untrusted Data
Improper Authentication
NULL Pointer Dereference
Use of Hard-coded Credentials
-
Improper Restriction of Operations within the Bounds of a Memory Buffer
Missing Authorization
Incorrect Default Permissions
-
Exposure of Sensitive Information to an Unauthorized Actor
-
Insufficiently Protected Credentials
-
Incorrect Permission Assignment for Critical Resource
-
Improper Restriction of XML External Entity Reference
-
Server-Side Request Forgery (SSRF)
-
Improper Neutralization of Special Elements used in a Command (Command Injection)

Want my team to demystify SaaS security for you so that you can make smart decisions?
How Do I Protect My SaaS Applications?
Your SaaS product is a constant security threat you should address. Hackers are always trying to access SaaS applications because they are hosted in the cloud. They can utilize any small loophole to gain control and steal customer data.
However, you can keep hackers at bay if you do the SaaS security best practices. You can think of using stronger authentication, vetting SaaS vendors, proper vulnerability management, and other application security best practices that help you become enterprise-ready.
What are SaaS Security Best Practices?
The list of the software security practices can be endless. But in the long run it will pay for you to try and build a culture of security in your software development team so that your investment in tools, processes and people keeps paying dividends in the long term.
Most web applications are never tested for security vulnerabilities by software developers so you can not allow yourself to relax. You still have to be stringent with security measures you put in place.
The first step is to start implementing the following best SaaS security practices:
Examine Your Cloud Assets and Document Their Usage
Understanding how your SaaS application works help to identify any threat on time before it becomes a disaster. So, you should examine how the software you or third-party access and manage.
A proper manifest document helps you know who what packages and frameworks are being used in your SaaS. It is the first critical step in data protection, as you will have a better understanding of when these packages and frameworks need to be updated.
Cloud platform scanning, technically referred to as CIS benchmarking, is the next step in protecting your cloud platform. This can be done via a cloud platform penetration testing services or via automated tools like Cyber Chief.
Set Sensitive Data Protection Policies
Data protection policies are not just requirements by regulating agencies but also SaaS application security. It provides a basic framework that guides data accessibility and usage. Ensure you have the procedure in place for application developers, analysts, and other staff with access privileges to sensitive data.
Setting data protection policies is vital if you have different teams of developers involved in different phases of the application’s development lifecycle. But remember to make the policies detailed enough for everyone to understand. There should be no ambiguity or flaws in them.
Data Encryption with Private Keys
Hackers deploy different strategies to access sensitive information from your application. They can use SQL injection, phishing attacks, or any other. That is where data encryption comes in.
Make your personal information or any sensitive data transmitted or stored in the database useless to any unauthorized party through encryption. Use a private key to encrypt any data. That is the same key you need to decrypt if you want to access the information.
Data encryption is vital for any SaaS application, especially those that collect customer data. Most data protection agencies make it mandatory for companies to encrypt personal and sensitive information collected from users. You can apply TLS 1.2 or 1.3 together with SSL encryption on both ends of the application. Using an SSL certificate from a reputable provider boosts trust among clients and web browsers.
Enact Cloud Data Deletion Policies
Most cloud service providers and users care much about the data storage and protection policies but forget the deletion policies. Most SaaS applications automatically generate data that become obsolete after some time. They may seem useless, but attackers can use them to harm the system.
Cloud data deletion policies should be set in place by software developers and vendors. Design and implement a procedure for removing unneeded data from the system. It can be within a week, month, or even a year, depending on its importance.
Some data protection laws legislate that software vendor allow users to delete the data you store for them and about them. But even if not for that, why don’t you make it a habit to check what you no longer use and determine when to delete them? Fortunately, you can automate the entire process. So, you won’t have to waste more time doing the same.
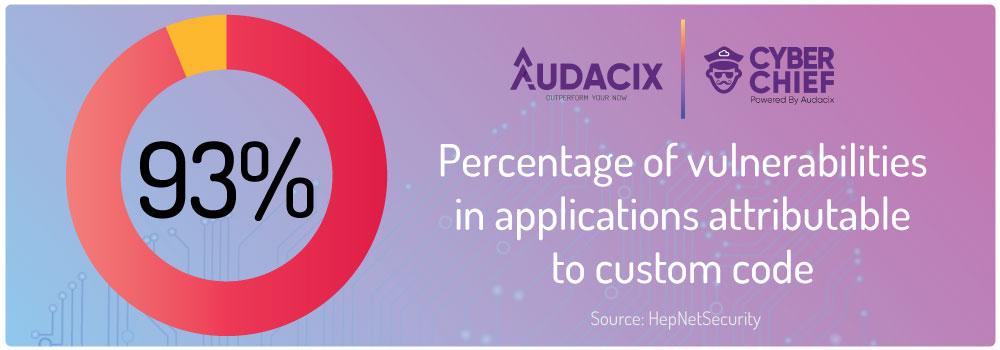
Perform Dynamic Vulnerability Scanning
Technology is fast changing, and hackers are finding new ways to attack your system. Your cloud application can be safe today and become vulnerable the next day. So, what do you need to do?
Vulnerability testing tools help to identify SaaS software security threats you need to address before cybercriminals notice them.
Vulnerability scanning tools give you an automated process to find vulnerabilities in your SaaS solution, which can be done statically or dynamically. One is not a substitute for the other. In fact, you should implement both to ensure all your SaaS applications are safe.
Static scanning reads the current software codes to identify any known vulnerabilities. On the other hand, dynamic vulnerability scanning is automated to conduct penetration tests on your application. You should do it every time you update the software in all your cloud applications.
online pentest tools designed just for this purpose are already available, and most are easy to use and affordable. So, your developers don’t have to be security experts to ensure that your SaaS solution has a strong security posture.

Perform Two Gray-Box Penetration Tests Annually
Web application penetration tests are often expensive and priceless at the same time. Testing your SaaS application’s security strength pays in the long run. You remain peaceful, knowing that the data is not compromised and still protected.
You should conduct a gray-box penetration test at least once a year if you import a few lines of code into your application annually. But if you are significantly involved in application upgrades and shipping codes weekly or monthly, consider doing it at least twice a year.
My team has created a pentesting-as-a-service solution tailor made for SaaS companies that help you put these practices in place in a frictionless manner.
Obtain ISO 27001 and/or SOC 2 Certifications
These certifications are proof of your trustworthiness from the auditing perspective. ISO 27001 certification shows that your SaaS application is immune to cyberattacks and free from all vulnerabilities.
On the other hand, SOC 2 certification proves that your company and security systems have been assessed and approved for compliance. This certification is widely recognized in North America.

Want my team to show you how to put a scaleable SaaS security structure in place?
Is There a SaaS Security Checklist That My Software Development Team Can Use?
Yes. Your security team can use the SaaS security checklist throughout the software development lifecycle. It helps your staff build critical security controls for sealing loopholes without spending a fortune on security matters.
A SaaS security checklist outlines must-have controls, a framework for regular in-house security checks, and risks of data breaches, among others. Download your copy of our popular SaaS security checklist to stay ahead of the attackers.
Are There SaaS Security Certifications That Will Help My SaaS Become Enterprise-Ready?
Yes. The most common and widely recognized SaaS security certifications are SOC 2 and ISO27001 accreditation. These two are used in different parts of the world and prove that your SaaS takes matters of data security seriously.
ISO 27001 is recognized worldwide except in North America. Choose SOC 2 certification if you do business in North America. It shows that your organization's management systems are audited by an independent body for compliance. You get recognized internationally for using the best SaaS security practices.
Can I Implement a Security Structure That Helps Strengthen the Security of My SaaS Application?
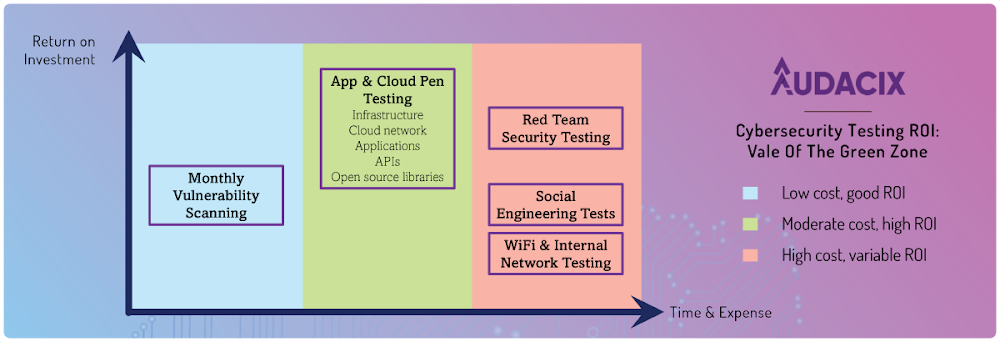
Yes. It is possible to implement different strategies that help you strengthen the security of your SaaS applications. Fortunately, tons of ways of doing it exist, which include the following:
Monthly vulnerability testing
App and cloud pen testing
Read team security testing
Social engineering testing
-
Wi-Fi and internal network testing
What Are the Components Of A SaaS-Security-As-A-Service Solution?
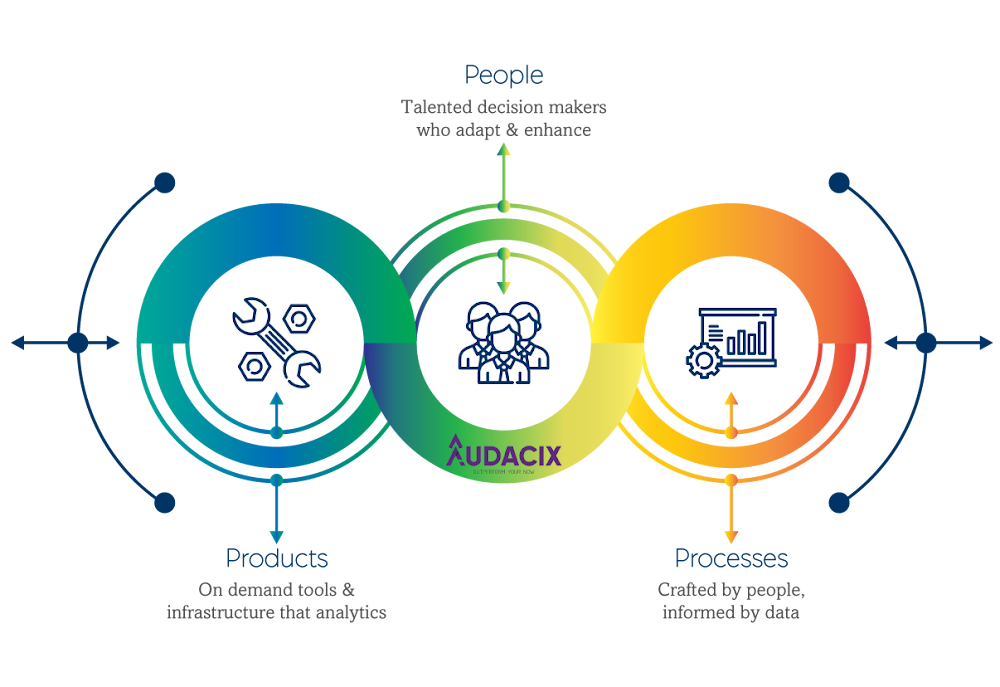
My team's SaaS security-as-a-service solution is a helpful approach in implementing security best practices for software companies. It combines three key players or components: product, people, and process.
It involves a talented team that makes crucial decisions based on the available data to adapt and enhance the process. And the result is on-demand tools and analytics.
Which Tools Can Help Me With SaaS Security Posture Management?
Different SaaS security posture management tools exist, but Cyber Chief is the most recommended. This online software has intuitive features for developers and managers that make the entire process straightforward. Try Cyber Chief for free to get an insight into what it offers.
You can also read this review of the best web app security testing tools, both of the paid and free varieties, to understand your options and work out which tool might be most suitable for your needs.
Remember, any tool you choose is only going to be as useful as how much your team ACTUALLY uses it. Otherwise, your purchase will just become another poor decision that results in wasted money.
This old piece of wisdom about ships holds true for SaaS security tools too!

How Do I Choose the Best SaaS Security Testing Vendor?
This video will give you some great tips on how to choose a SaaS security partner that gives you maximum bang for your buck:
Your choice of a SaaS security testing vendor depends on many factors. You should ask yourself many questions and provide answers to help you make the best decision. Consider the following:
-
Do your customers ask for certain security reports before they agree to use your SaaS?
-
How will your chosen penetration testing company give you the depth and breadth of testing you need?
-
How will your chosen partner help you build security into your software development process?
How will your team communicate with relevant security experts on a daily basis?
-
How will you measure ROI from the project (remember, ROI from application security can rarely be measured just on the frontend cost)?
Does your SaaS security partner understand the nuances and challenges of your software development workflows?
The most obvious page to get more information about what my team does for SaaS companies like yours is from our SaaS & web app penetration testing services page.
Or you can take a positive next step and get real answers that are specific to your situation by booking a discovery call with my team. On this call my team will help you understand how you can get to the next phase of your SaaS security journey.





